A massive infostealer malware campaign has exposed 183 million email addresses and matching passwords online, according to the Have I Been Pwned (HIBP) security service. The data, compiled from malware infection logs, was added to HIBP’s searchable database on October 21.
Key Takeaways
- 183 million email credentials exposed via infostealer malware
- Data comes from malware logs, not a direct Google breach
- Check your account status at Have I Been Pwned website
- Enable two-factor authentication for protection
Google has responded to the reports, stating claims of a Gmail security breach are “false” and that “Gmail’s defenses are strong, and users remain protected.”
How to Check if Your Gmail Account Is Compromised
Visit the official Have I Been Pwned website at haveibeenpwned.com and enter your email address in the search page. The service will immediately tell you if your credentials appear in the breach.
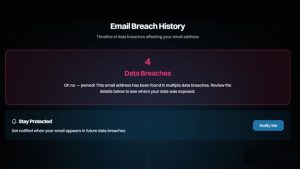
- If compromised: Message shows “Oh no — pwned!”
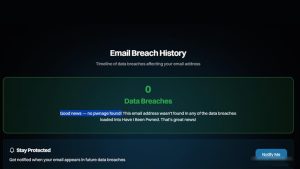
- If safe: Message shows “Good news — no pwnage found!”
What to Do If Your Account Is Compromised
For individual users:
- Enable two-step verification in Gmail security settings
- Change your password immediately
- Use hardware keys or passkeys instead of SMS for stronger protection
For organizations:
- Strengthen password policies and mandate multi-factor authentication (MFA)
- Improve anti-malware defenses to prevent future infections
- Enabling MFA remains one of the most effective methods to protect against unauthorized access
The exposed dataset, named “Synthient Stealer Log Threat Data Data Breach,” was compiled by Synthient LLC and originated from infostealer malware infection logs. The breach occurred in April this year, according to HIBP.